
Mechsoft Technologies’ 24×7 SOC-as-a-Service, together with cutting-edge threat intelligence and knowledgeable defenders, will help you defend against the most complex threats.
Security Operations Center (SOC) plays a crucial role in an organization’s ability to sustain operations, remain profitable, and achieve and maintain compliance with applicable regulations.
But building and maintaining an internal Security Operation Center, that can achieve a high level of security maturity- can turn out to be costly and time-consuming.
Due to a lack of resources and expertise, not every company can build its own Security Operation Center. The underlying costs, hiring the right experts, and managing the technology stack can become overwhelming.
Mechsoft SOC as a Service delivers all of the benefits of a dedicated 24/7 SOC, but without the high costs, complexity, and frustrations that come with building, staffing, and managing one in-house.
Get a comprehensive cyber security model, including Managed Detection and Response (MDR), SIEM capabilities, SOC experts, etc., to secure your business. With the effective combination of people, products, and processes, we can help detect advanced threats and contain them before they impact your business.
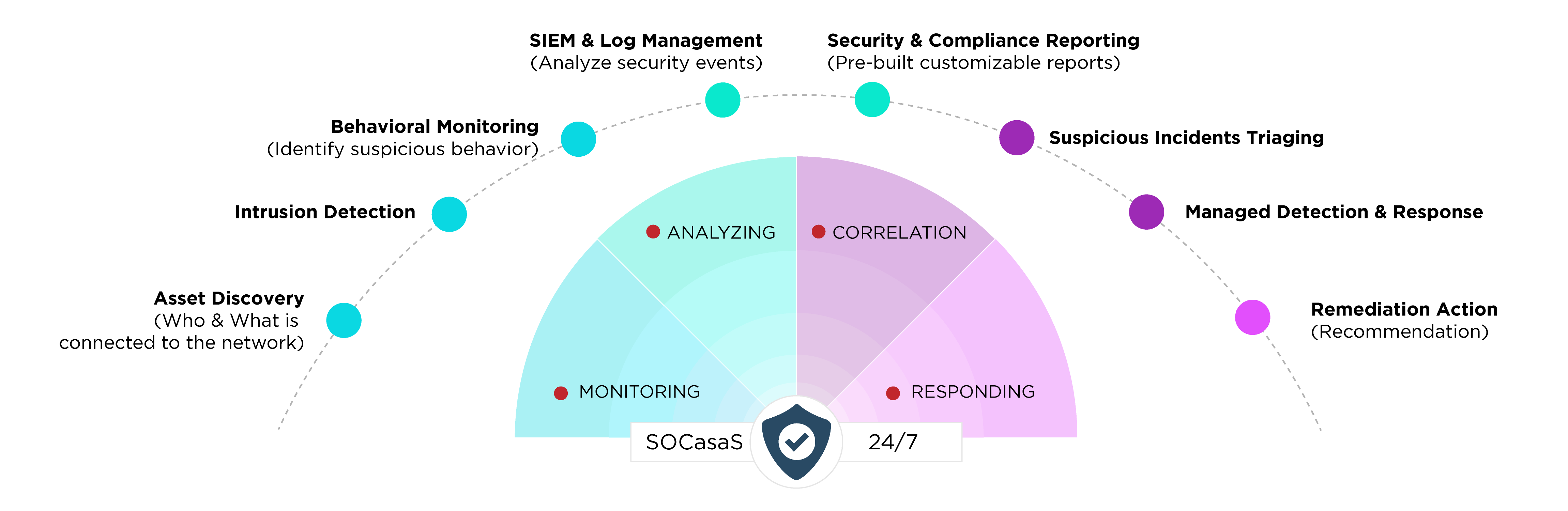
The SOC team consists of 3 different tiers of SOC analysts and dedicated managers.
Tier 1 analysts are mainly responsible for collecting raw data as well as reviewing alarms and alerts. They need to confirm, determine, or adjust the criticality of alerts. They also enrich them with relevant data.
For every alert, the triage specialist has to identify whether it’s justified or a false positive. Alert fatigue is a real issue.If tier 1 analysts cannot solve occurring problems, they must escalate them to tier 2 analysts.
At tier 2, analysts review higher-priority security incidents. Triage specialists escalate these incidents. They perform a more in-depth assessment using threat intelligence. They need to understand the scope of an attack and be aware of the affected systems.
This second tier transforms the raw attack telemetry data collected at tier 1. It turns it into actionable threat intelligence. Incident responders design and implement strategies to contain and recover from an incident. They are responsible for this.
If a tier 2 analyst faces major challenges in identifying or mitigating an attack, they consult other tier 2 analysts. If necessary, they escalate the incident to tier 3.
Tier 3 analysts are the most experienced workforce in a SOC. They handle major incidents escalated to them by the incident responders. They also perform or at least supervise vulnerability assessments. They conduct penetration tests to identify possible attack vectors.
Their most important responsibility is to proactively identify possible threats, security gaps, and vulnerabilities. These may be unknown.
They should also recommend ways to optimize the deployed security monitoring tools. They can do this as they gain reasonable knowledge about possible threat detection to the systems.
SOC managers supervise the security operations team. They provide technical guidance if needed, but most importantly, they are in charge of adequately managing the team.
This includes hiring, training and evaluating team members; creating processes; assessing incident reports; and developing and implementing necessary crisis communication plans.
They also oversee the financial aspects of a SOC, support security audits, and report to the chief information security officer (CISO) or a respective top-level management position.
© 2024 Mechsoft Technologies. All Rights Reserved.